Cyber Security Services
Guarding Your Data, Reputation, Compliance & Peace of Mind


Risk
Reduction

Trusted
Expertise

24/7
Support

Pain-Free
Compliance
Our Cyber Security Services
Cyber Essentials
Cyber Essentials Plus
IASME Cyber Baseline
IASME Cyber Assurance
Cyber Security Auditing
Penetration Testing
Vulnerability Scanning & DAST
GDPR Compliance
SIEM/SOC Services
Phishing Testing
Training
Contact us
Who We Help
The
BUSY
SME OWNER
"Cybersecurity seems complex, and I'm not sure why it's crucial for my small business."
The
Compliance
"I need to be cyber essentials compliant to stay competitive, but I want to keep it straightforward."
The
Delegating
"I assumed my IT support had cybersecurity covered, and now I'm not so sure. What should I be asking them?"
Will Your Staff Get You Hacked?
With more than 80% of data breaches being attributable to a member of staff, how safe is YOUR business?
This completely catch-free quiz will take less than 5 minutes and help you to understand how likely your staff are to be your downfall.


Will Your Staff Get You Hacked?
It’s a startling truth — nearly half of all UK SMEs experienced a cyber attack last year, as per the latest findings from government reports. Even more concerning is the trend of increasing incidents, with a significant number of businesses facing the aftermath of an attack.
The cyber threat landscape is evolving faster than ever, and there’s a growing gap in cyber defense skills globally. In fact, a majority of UK businesses acknowledge a critical shortage in cybersecurity expertise internally.
Financial motives drive the majority of cyber breaches, as Verizon’s studies indicate, with many going undetected for extended periods. However, the Online Trust Alliance reminds us that basic cybersecurity measures can prevent the vast majority of these incidents.
Reacting after a breach is costly and stressful. Unity Metrix stands ready to help you take proactive steps now, fortifying your business’s defenses and ensuring you are prepared, not just for today’s challenges but for tomorrow’s threats. The time to strengthen your cybersecurity is now — let’s ensure your business is not just another statistic.
65 %
65%
of medium-sized businesses were hit by a cyber attack in the latest UK government survey
71 %
71%
of breaches are financially motivated
95 %
95%
of incidents can be prevented
Our Process

Assessment
& Planning
We start with a cyber health check to understand your current security posture and identify vulnerabilities
Pinpointing your cyber strengths and weaknesses

Customised
Solution Design
Our experts craft a cybersecurity strategy tailored to your business's unique needs and compliance requirements
A tailor-made defense for your digital assets

Implementation
& Training
We put our plan into action, bolstering your defenses and providing training to empower your team
Elevate your team's
cyber savvy

Monitoring &
Ongoing Support
With continuous monitoring and support, we ensure your defences stay robust against evolving threats
Keeping watch, keeping you secure

What Our Customers Say About us
Frequently Asked Questions
How much do cyber security services cost?
The cost of cybersecurity services varies based on your business’s size, complexity, and specific needs. You can see some guideline pricing here and for a tailored quote, please contact us to discuss your requirements.
How does Unity Metrix compare to other cyber security providers?
Unity Metrix stands out by offering comprehensive, customised cybersecurity solutions tailored specifically for SMEs. We combine technical measures with governance and compliance, ensuring your business is fully protected and compliant. Our approach is designed to meet the unique needs of smaller enterprises, providing robust security without overwhelming your resources.
What are the top cyber security risks for SMEs today?
Top cybersecurity risks for SMEs include phishing attacks, ransomware, data breaches, and weak password practices. Staying informed and implementing robust security measures can mitigate these risks.
What happens if a cyber breach occurs?
In the event of a cyber breach, Unity Metrix provides immediate support to contain and mitigate the impact. We also help you develop and implement a recovery plan to restore normal operations swiftly.
What should I look for when choosing a cyber security service?
When choosing a cybersecurity service, look for providers with a proven track record, comprehensive solutions that include both technical and governance measures, and strong customer support.
Doesn’t my existing IT company handle my cyber security?
While your IT company may provide some security measures, specialised cybersecurity services like those from Unity Metrix offer a deeper focus on protecting against sophisticated threats and ensuring compliance.
Can Unity Metrix ensure my company is compliant with regulations like GDPR?
Yes, Unity Metrix helps your business comply with regulations like GDPR by implementing comprehensive cybersecurity measures and governance frameworks that align with regulatory standards.
How long does it take to implement cyber security measures?
The time required to implement cybersecurity measures varies depending on your business’s size and complexity. Unity Metrix works efficiently to deploy effective security solutions promptly while ensuring minimal disruption to your operations.
Latest News
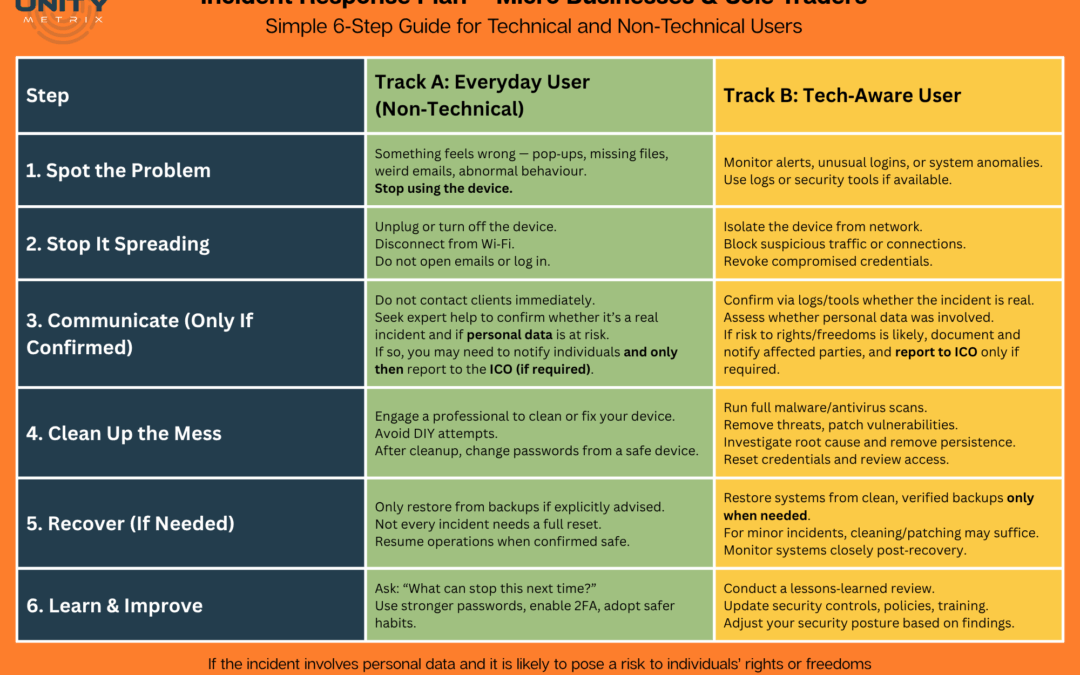
Free Incident Response Plan Poster
Download our Free Incident Response Plan for Small Businesses – a simple 6-step cyber security guide for sole traders and micro businesses. Created by Unity Metrix for Cyber Security Awareness Month 2025.

Marks & Spencer – What Happened & Why You Should Care
In early 2025, Marks & Spencer was hit by a sophisticated cyberattack involving social engineering, SIM-swap fraud, and ransomware. Customer data was stolen, services were disrupted, and the incident exposed the growing weakness of SMS-based security. This article breaks down what happened, why it matters, and how you can protect yourself.
Why a VPN is Your #1 Priority: Essential Advice for Expats and Remote Workers
Stay connected and secure as an expat or remote worker with NordVPN. Access geo-restricted content, protect your data on public Wi-Fi, and enjoy fast, encrypted connections anywhere in the world. Stream, work, and browse with confidence.
👉 Get NordVPN today and secure your digital future!

Do I need a penetration test?
Do I need a penetration test? If you have a website that takes information about users… If you have a website that takes credit cards… If you have an internal system that shares personal information with external bodies… If you develop systems that will hold personal...

Why is penetration testing required and why is it so important?
Penetration testing is required for two main reasons: Everyone makes mistakes! In Microsoft Windows for instance there are over a 50 million lines of code, there are definitely going to be mistakes, and some can be costly. Hackers actively look for those mistakes....

How do you perform a vulnerability scan?
How do you perform a vulnerability scan? A vulnerability scan is performed by a piece of software that resides either on a system inside the network, or more often on a cloud service. Modern scanners are very powerful and have a lot of automation built-in, so for a...

Vulnerability scanning
What does vulnerability scanning do? Vulnerability scanning is the process of scanning software and systems for known vulnerabilities. A vulnerability scanner will maintain and refer to a massive database of known vulnerabilities in order to compare and classify...

Datto ALTO 3 Explained

What is a virtual CISO? When and how to hire one
Chief information security officers (CISOs) are in high demand, and good ones are expensive and difficult to find. Following a rash of high-profile data breaches, and knowing that such breaches have far-reaching consequences that are far more costly than the cost of...

Penetration Testing vs Vulnerability Scanning
Penetration testing and vulnerability scanning are often confused as the same service. This leads to business owners purchasing one when they really need the other. Below, we will outline the differences between the two to help better your understanding and ascertain which service your business requires.
Meet the founder
From our humble beginnings to becoming a trusted name in the cybersecurity industry, our journey is a testament to our commitment to innovation and excellence. But we’re not just tech geeks huddled around computer screens all day! We are a group of passionate individuals who believe that a safer digital world is not just a necessity but a right for every business out there. Our vision and hard work have propelled us into partnerships with diverse industries, from healthcare to e-commerce and everything in between.

Our Core Values

Transparency
We operate with an open-book policy. No hidden fees, no ambiguous language. We believe informed clients are the best clients.

Excellence
We never compromise on quality. Our services are designed to not just meet but exceed industry standards. Our certifications, including IASME Cyber Assurance Level 2, speak for themselves.

Innovation
Cyber threats evolve every day, and so do we. Continual training, research, and development keep us ahead of the curve and you out of harm’s way.

Customer-Centric
Your security is our success. Our 24/7 availability ensures that your business operations never have to pause because of a cybersecurity concern.
Get in Touch
