Compliance officers will appreciate how our services align with critical standards such as PCI DSS, ISO 27001, and GDPR, easing compliance burdens and demonstrating a proactive security stance.
For tech leaders and entrepreneurs in dynamic sectors like e-commerce and tech startups, our solutions fortify your ventures against cyber threats, enabling secure and sustainable growth.
We also empower data guardians and cybersecurity stewards by demystifying cybersecurity complexities, offering clear, actionable insights to streamline security management and enhance team awareness.
Partnering with Unity Metrix gives you more than just testing; you gain a strategic ally in navigating cyber threats, helping manage costs efficiently and fortify every layer of your organisation against evolving threats. This partnership allows you to focus on driving your business forward with confidence.
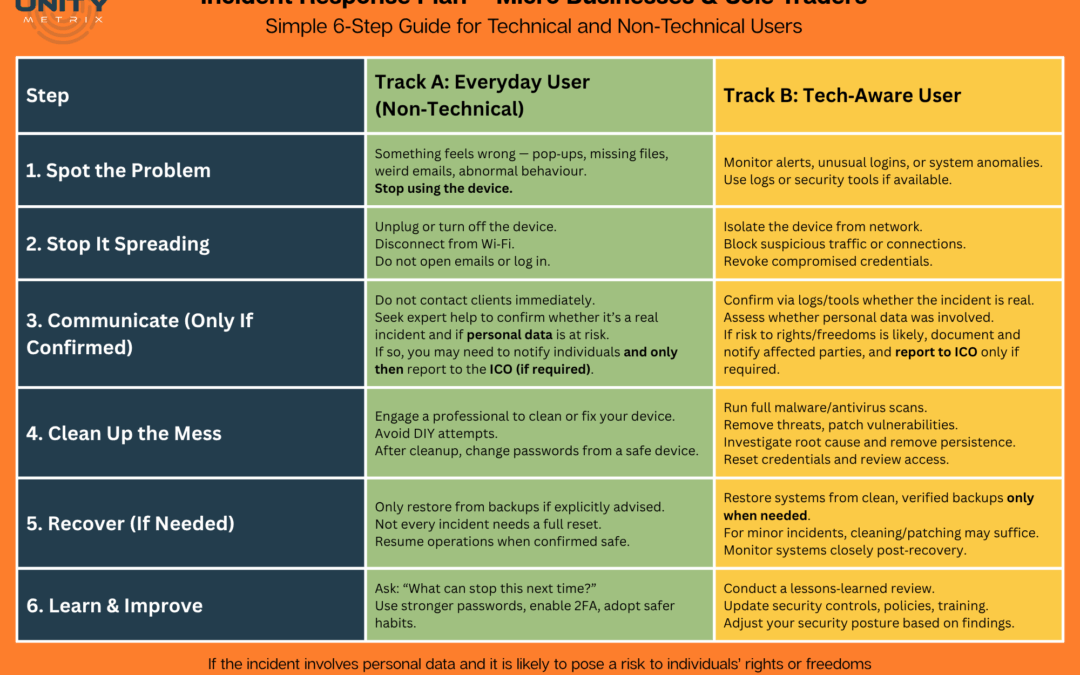
Why Choose Unity Metrix for Penetration Testing?
Precise Vulnerability Detection
Customised Security Evaluations
Direct Remediation Support
Intuitive Risk Dashboard
How Can You Benefit from a Pen Test?
Earn Customer Trust
Ensure Compliance
Simplify Security Management
Information Security Penetration Testing Costs Uncovered: How Much to Budget for Cyber Security
Basic Web Application Pen Test
Network Penetration Testing:
Full-Spectrum Testing:
Choose Your Pen Test: Comparing Web, Network, and Full-Spectrum Options
Web Application Penetration Testing
Network Penetration Testing
Full-Spectrum Testing
Avoid Compliance Nightmares: Pen Testing for GDPR, PCI DSS, and ISO 27001
GDPR
Helps ensure that personal data is protected against unauthorised access by identifying security weaknesses. Meeting the brief of Article 32 in “testing, assessing and evaluating the effectiveness of technical and organisational measures”
PCI DSS
Assesses the security of cardholder data by testing the network and application layers as per PCI DSS Requirement 11.4 “External and internal penetration testing is regularly performed, and exploitable vulnerabilities and security weaknesses are corrected.”
ISO 27001
Supports the establishment of an effective information security management system by identifying vulnerabilities and security gaps. ISO27001 12.6.1 states that exposure to vulnerabilities should be evaluated, and appropriate measures taken to address the associated risk