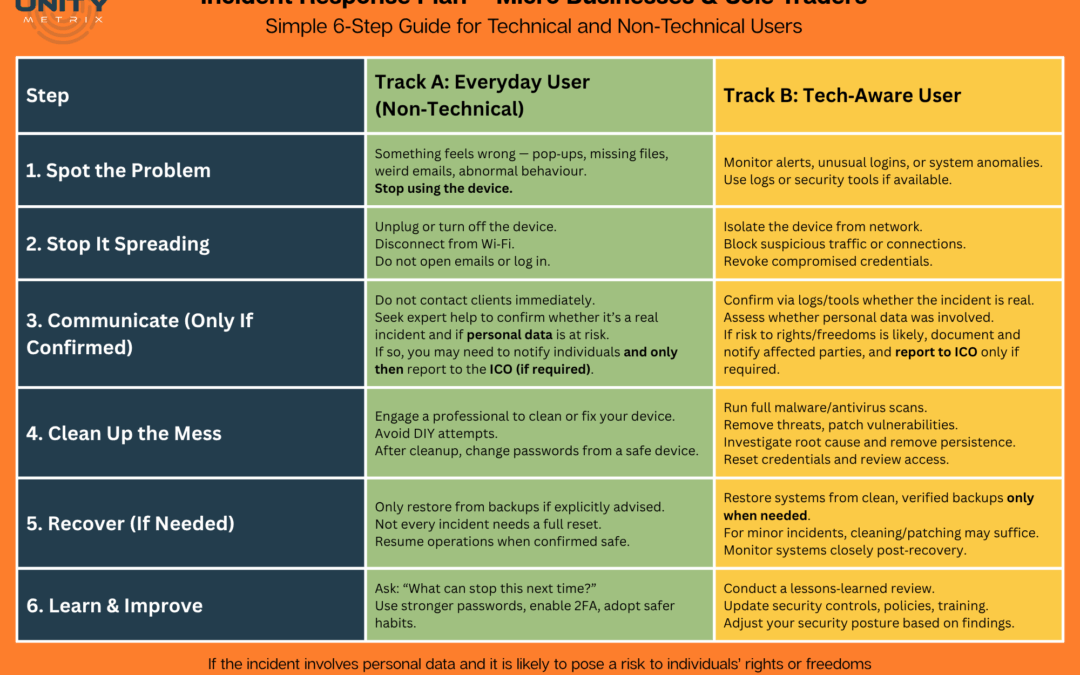
The results of these scans make it very clear exactly where the vulnerability lies, what it is and how you can resolve it. This can be anything from indicating a misconfiguration within a device, to identifying un-patched operating systems and default passwords.
- Cost-effective pro-active risk reduction
- Dynamic Application Security Testing (DAST)
- Infrastructure vulnerability testing
- DIY or managed service
- Scan infrastructure and web applications for thousands of vulnerabilities, continuously
- Netsparker, Appcheck and Acunetix partners
The second main type of scan is that of an application, and these days in particular a web application. This type of scan is known as a Dynamic Application Security Test, or DAST. These scanners work by interrogating an application for entry points and functions that can be prodded and poked and fed data with the intention of eliciting results that highlight vulnerabilities in the code and hosting systems. Advanced scanners also allow scripts, APIs and other real-time functions that help the scanner to emulate a real user (by logging in to the system for instance) thus providing a more realistic and thorough scan.
Many standards, including ISO27001, IASME Governance, Cyber Essentials, PCI DSS and GDPR expect that vulnerability scanning should be a key component of the modern business and include provisions within their
Unity Metrix partner with some of the biggest names in vulnerability scanning and are happy to provide licences for internal use of the relevant platform, or a fully managed service, offering monthly reports on security findings. In either case you will have access to full-blown reporting that identifies in details exactly where the issues are and how that can be resolved.